1.6 KiB
1.6 KiB
Homework 3: Cracking WiFI!
Crack the NetSec WiFi network password with bettercap
Find the BSSID and connected client of the NetSec Network
Perform a deauth attack on the network with bettercap and capture the 4-way handshake
Use the hcx toolsuite to convert the captured handshake to a format that hashcat can understand
Crack the password using hashcat and rockyou.txt
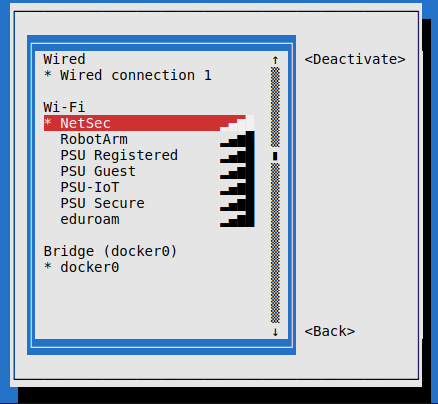
Connect workstation to the wifi network and show using nmtui
Now that I have found the password, I can initiate a wifi connection from mallory to the raspberry pi
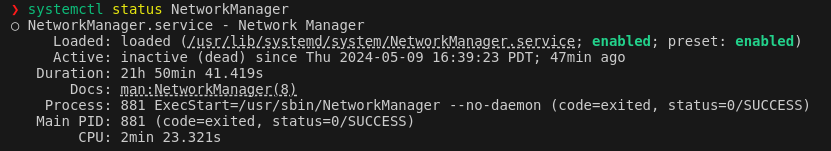
The first issue encountered was the the network manager was inactive. This is confirmed by running systemctl status NetworkManager
This was fixed by running sudo systemctl start NetworkManager
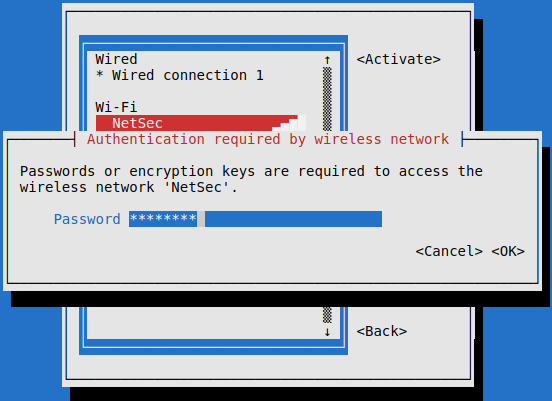
Now with sudo nmtui I can finally attempt connect to NetSec with the password, crackme1.
The connection was successfull
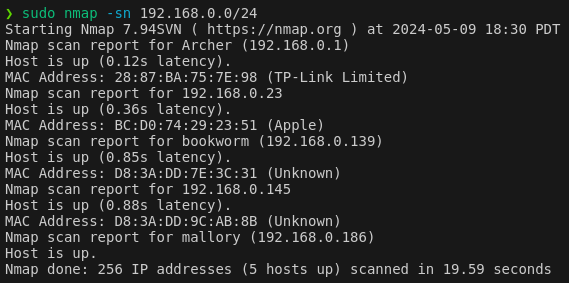
Scan the network with nmap
I now want to scan the network to identify the router, and devices connected to the router. A quick check with iwconfig and looking at the wlan0 interface shows that as a client of this router, we are in the subnet 192.168.0.0/24
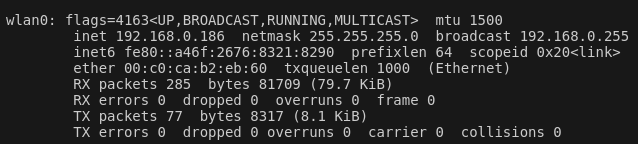
Now running sudo nmap -sn 192.168.0.0/24 (a simple ping scan) we have some interesting results.