2.8 KiB
Homework 5: Fuzzing
Prelude
The first step I took for this asignment was setting up the docker container. This was straightforward with the provided instructions
Part 1 - Tutorial
Step-0
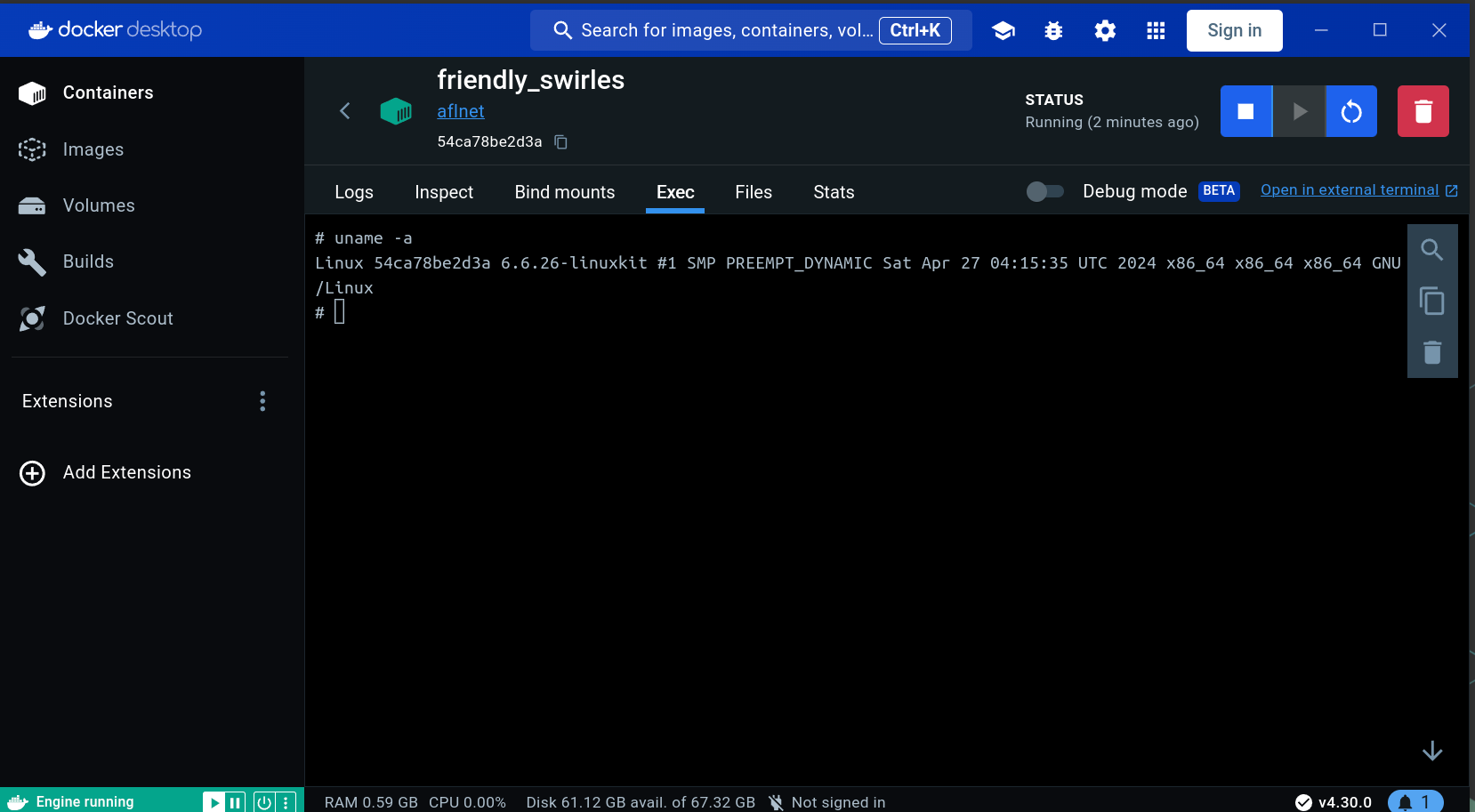
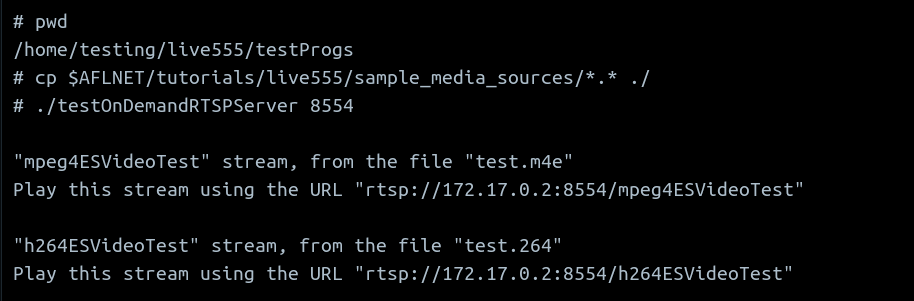
Here, I have followed the instructions the run the sample RTSP client and server
The server running is shown here
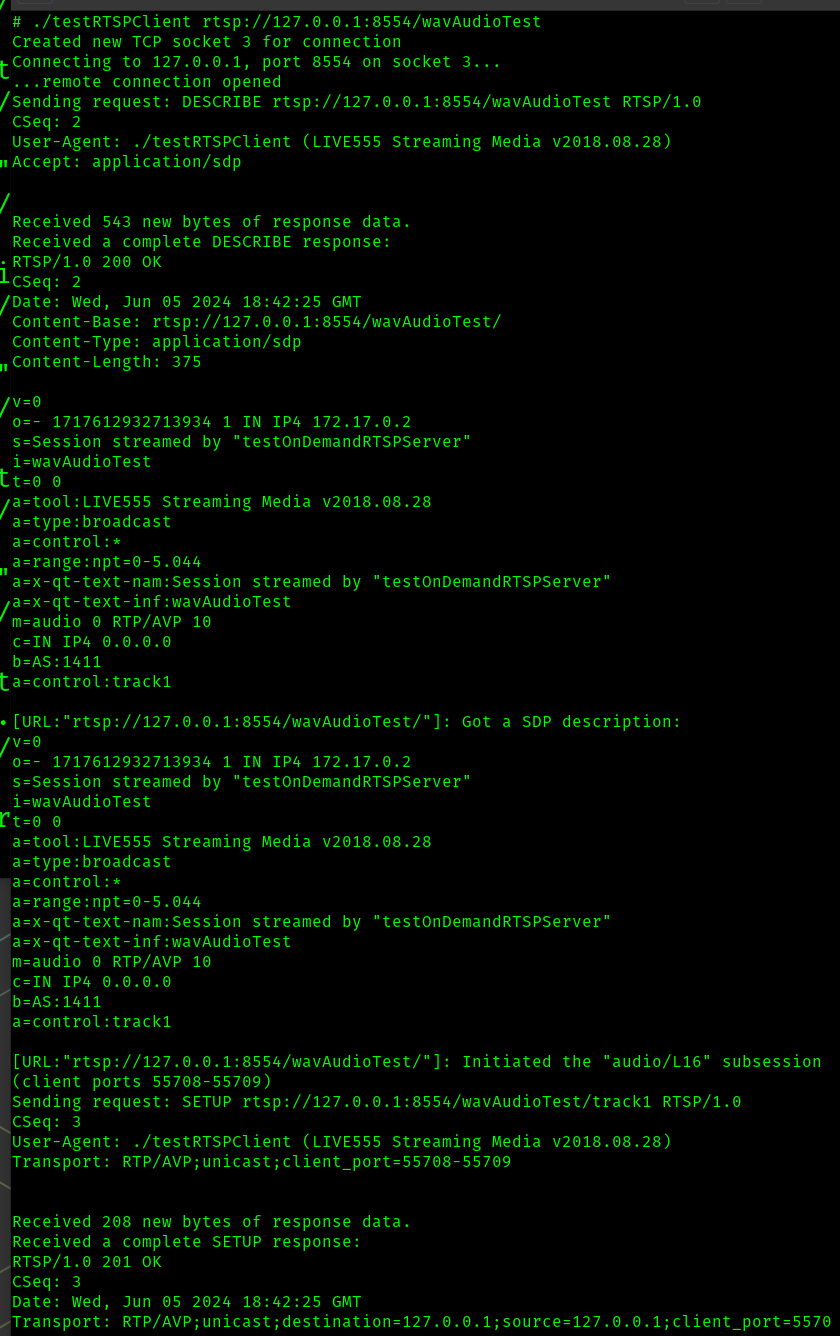
In another terminal, we run the sample client
Step-1. Prepare message sequences as seed inputs
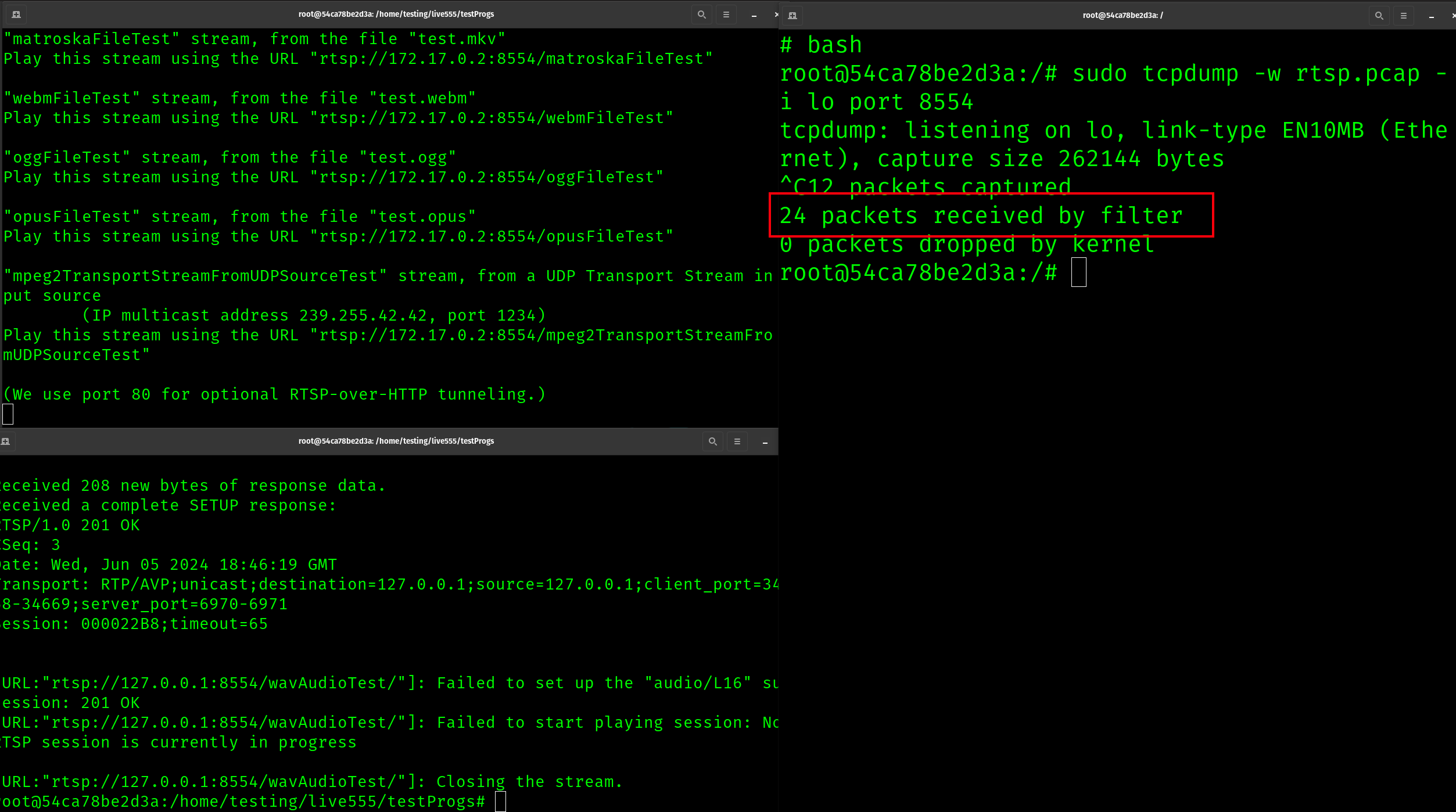
At this point, we have the server and client running. The next step is to install TCP dump, and open it up on a 3rd terminal window. We can now restart the client and capture some traffic
As we can see, with this approach we have captured 24 packets
Using docker cp I have copied that file rtsp.pcap to my local machine, and also have included it at ./rtsp.pcap
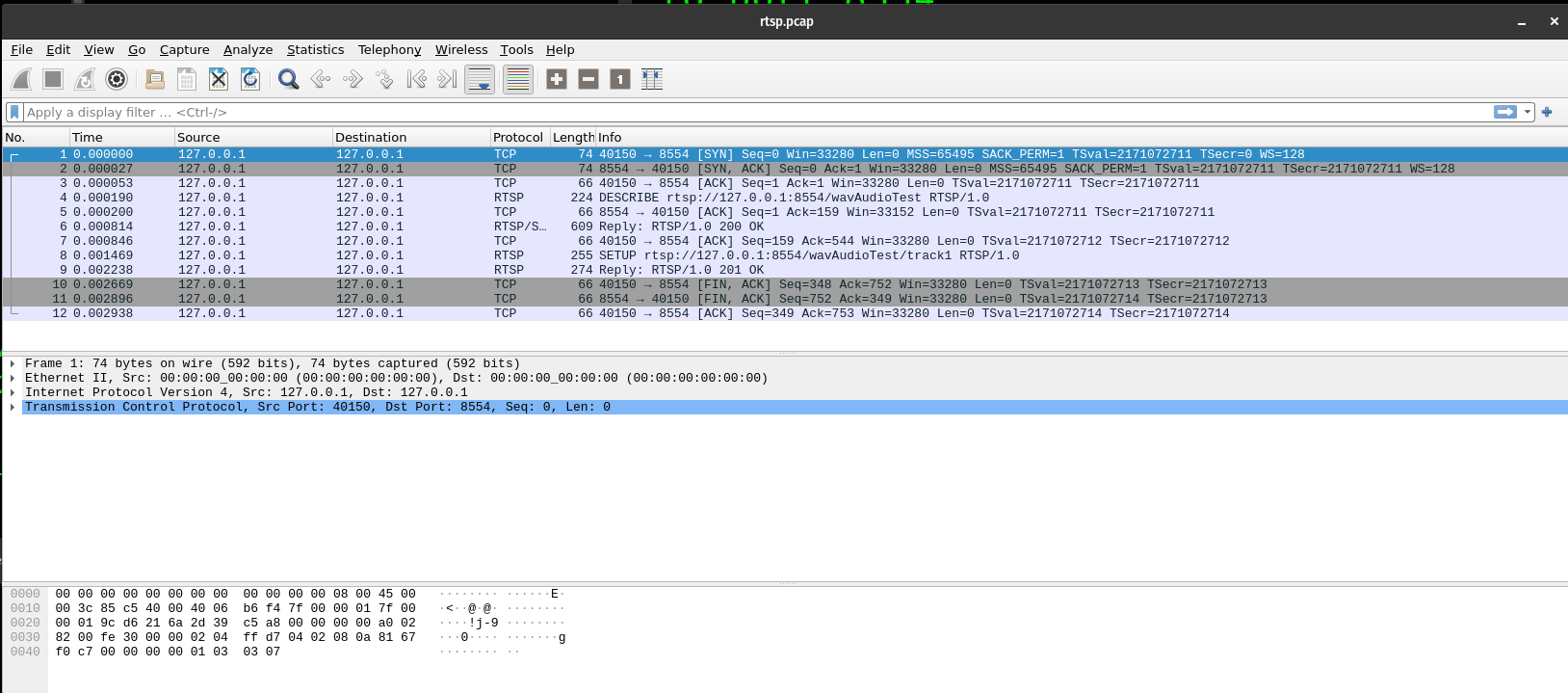
Lets take a look at this file with wireshark rtsp.pcap
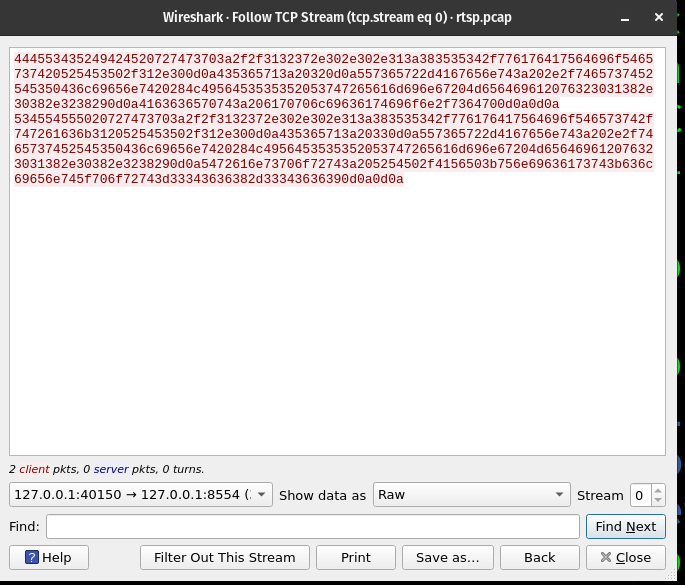
Following the instruction, we can save the raw TCP stream of the request messages to rtsp_requests_wav.raw
Step-2 Modifications
As understood in the Step 0 instructions, we have already applied the ceeb4f4 patch to make fuzzing more effective.
Step-3 Fuzzing
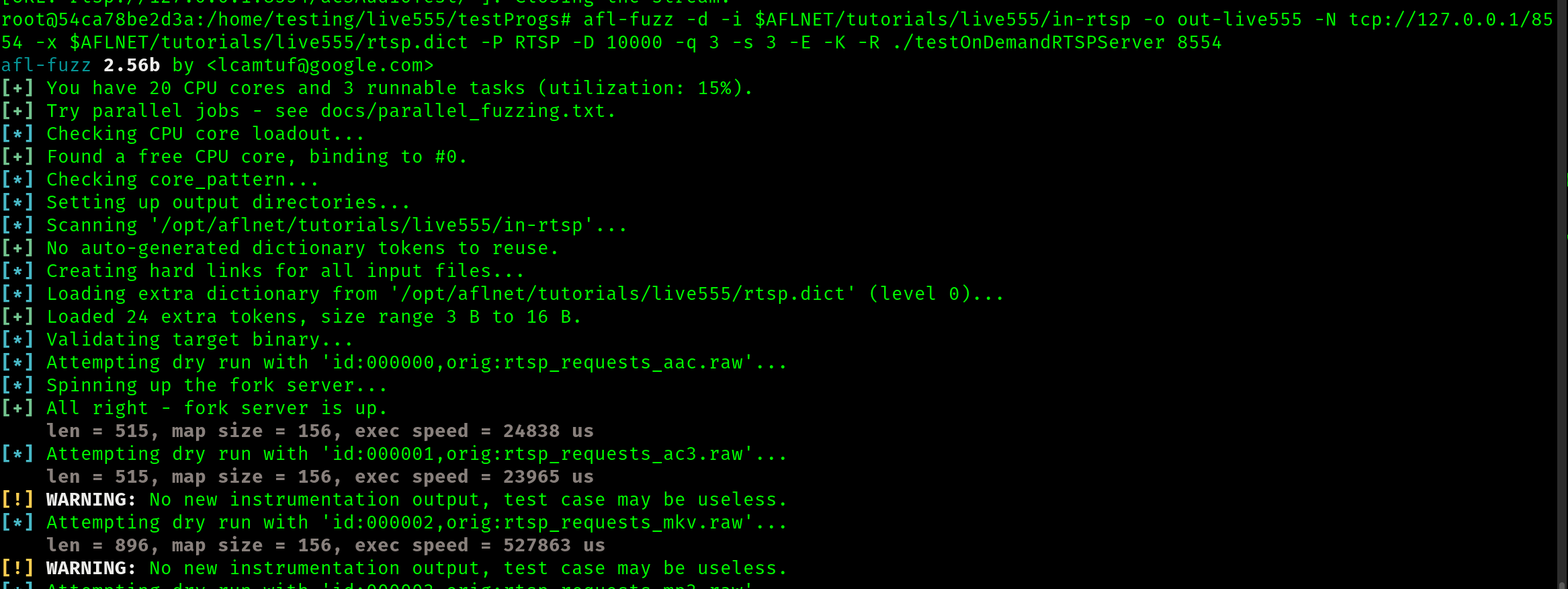
We begin the fuzzing process running the supplied command
afl-fuzz -d -i $AFLNET/tutorials/live555/in-rtsp -o out-live555 -N tcp://127.0.0.1/8554 -x $AFLNET/tutorials/live555/rtsp.dict -P RTSP -D 10000 -q 3 -s 3 -E -K -R ./testOnDemandRTSPServer 8554
It seems off to a good start, and I will let this run for some time and check back later. In this case, I will use the provided seed corpus.
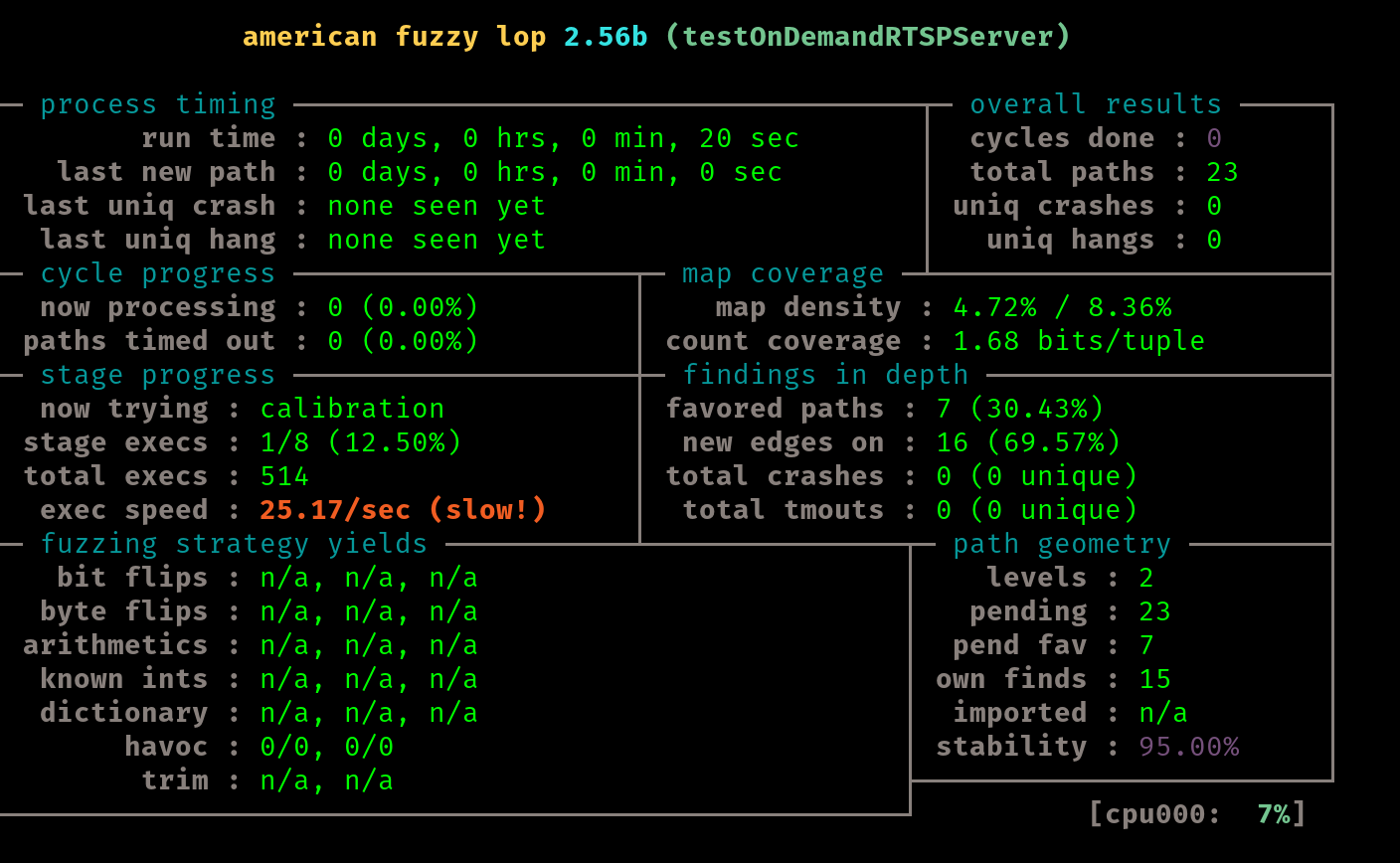
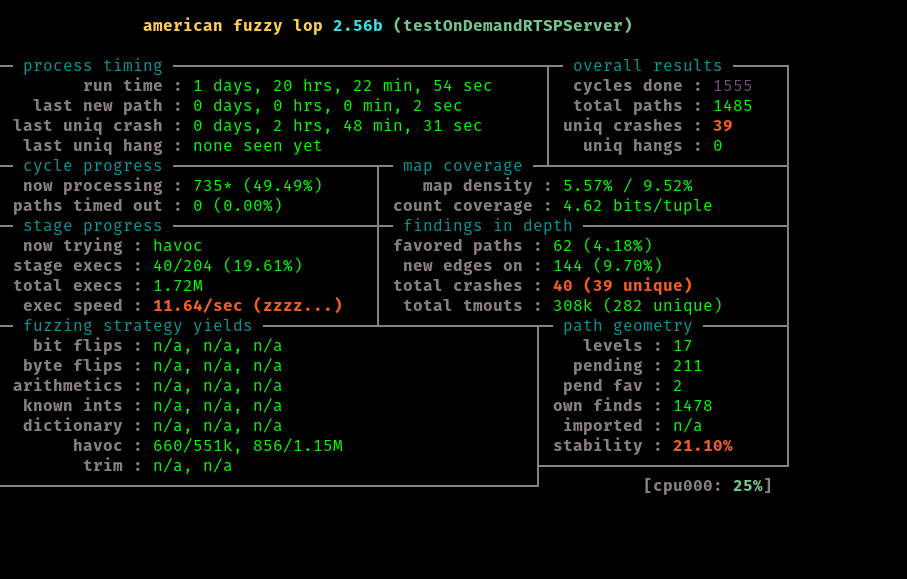
After about 44 hours of running this test it is time to move on. We notice we have 40 unique craches at this point, and the last one found was about 3 hours ago
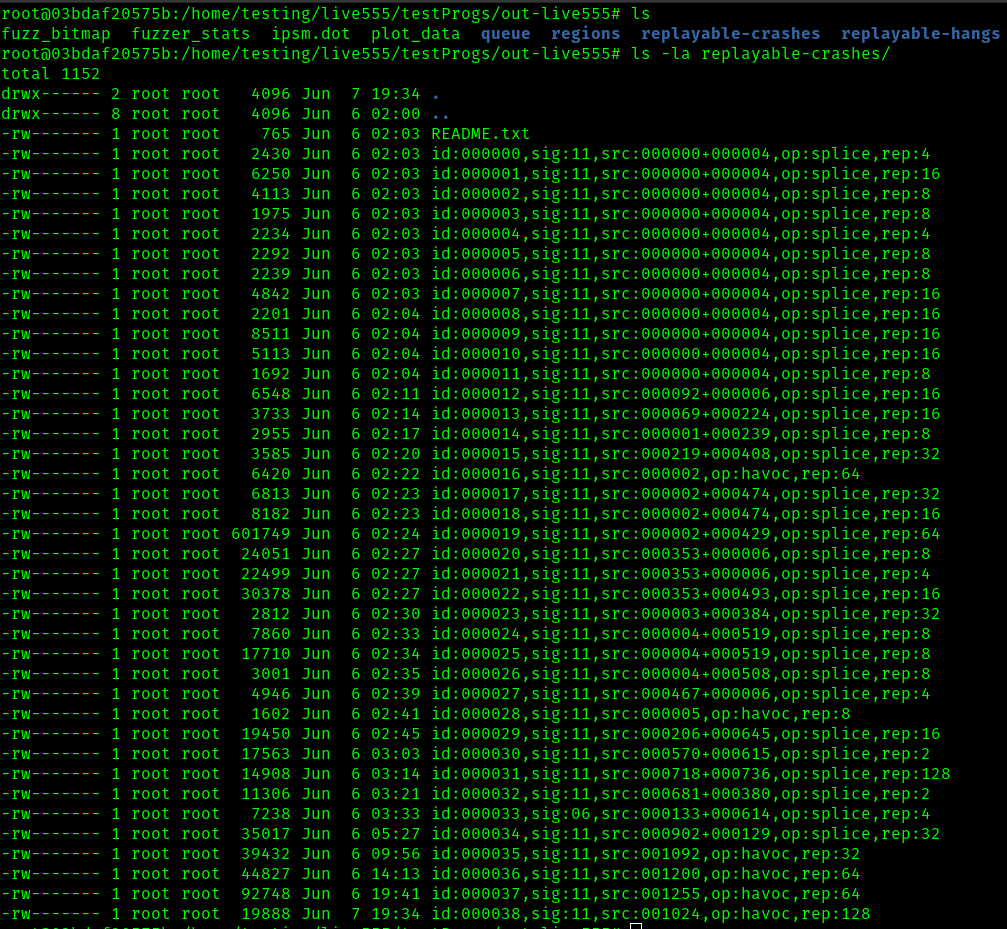
These crashes can be found in the replayable-crashes directory of our run
Step-4 Reproducing
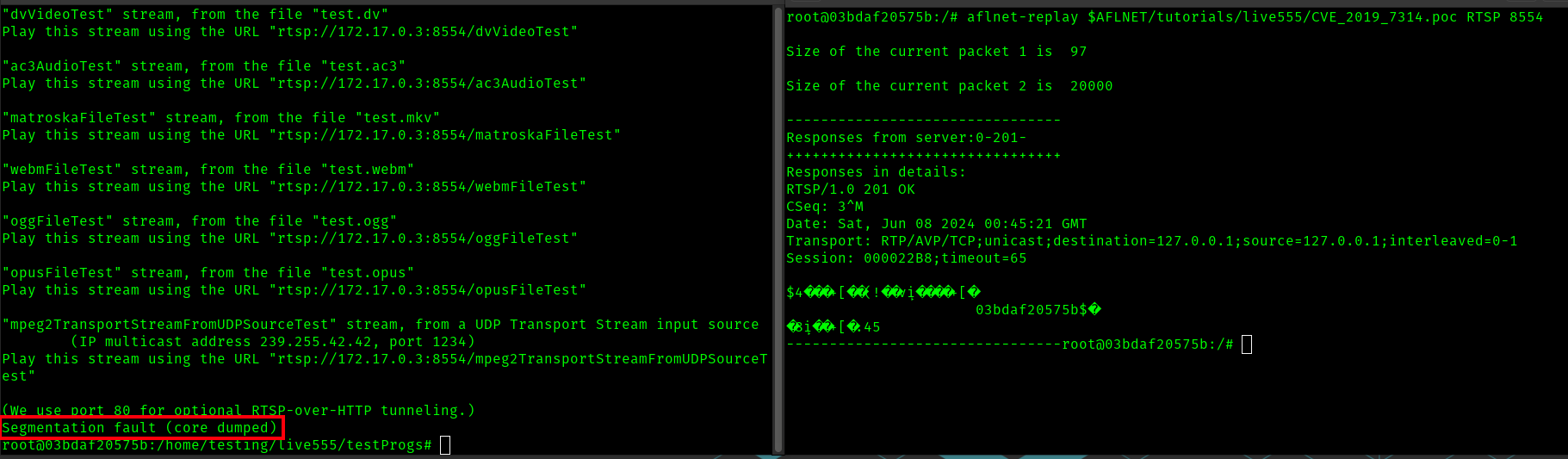
As noted in the instructions, with afl-replay we can replay the crashing client input on the running test server, as shown with the provided example input CVS_2019_7314.poc
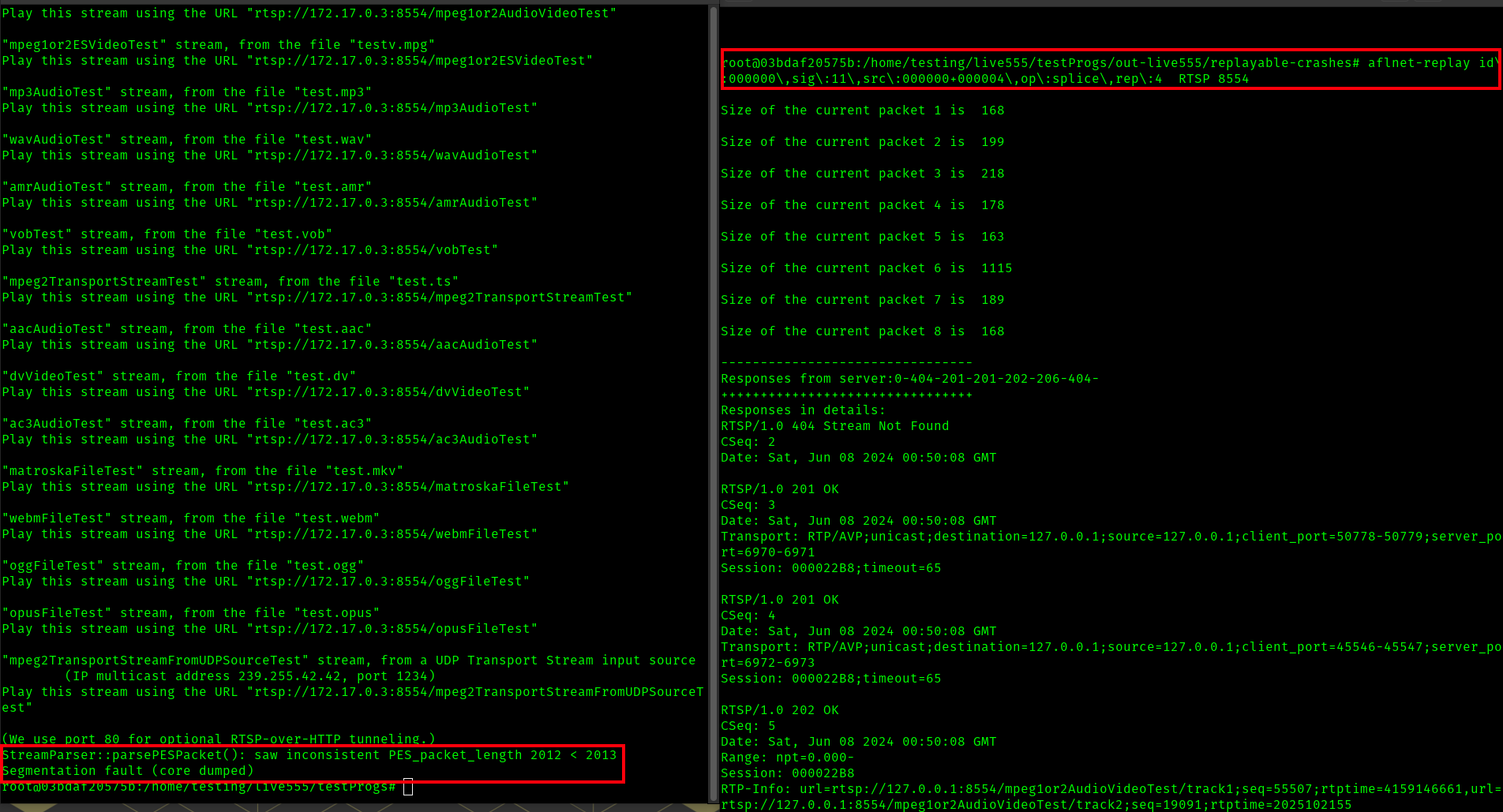
Here is another example of performing and aflnet-replay with one of the replayable crashes results I found to again crash the RTSP server
Part 2 - Our own example
I will run through this exercise again choosing my own example