1.5 KiB
Homework 3: Find the firmware
We start by copying the firmware capture file from ada to our machine
Reverse Engineering
First lets open this capture up in wireshark and do a high level overview
Wireshark overview
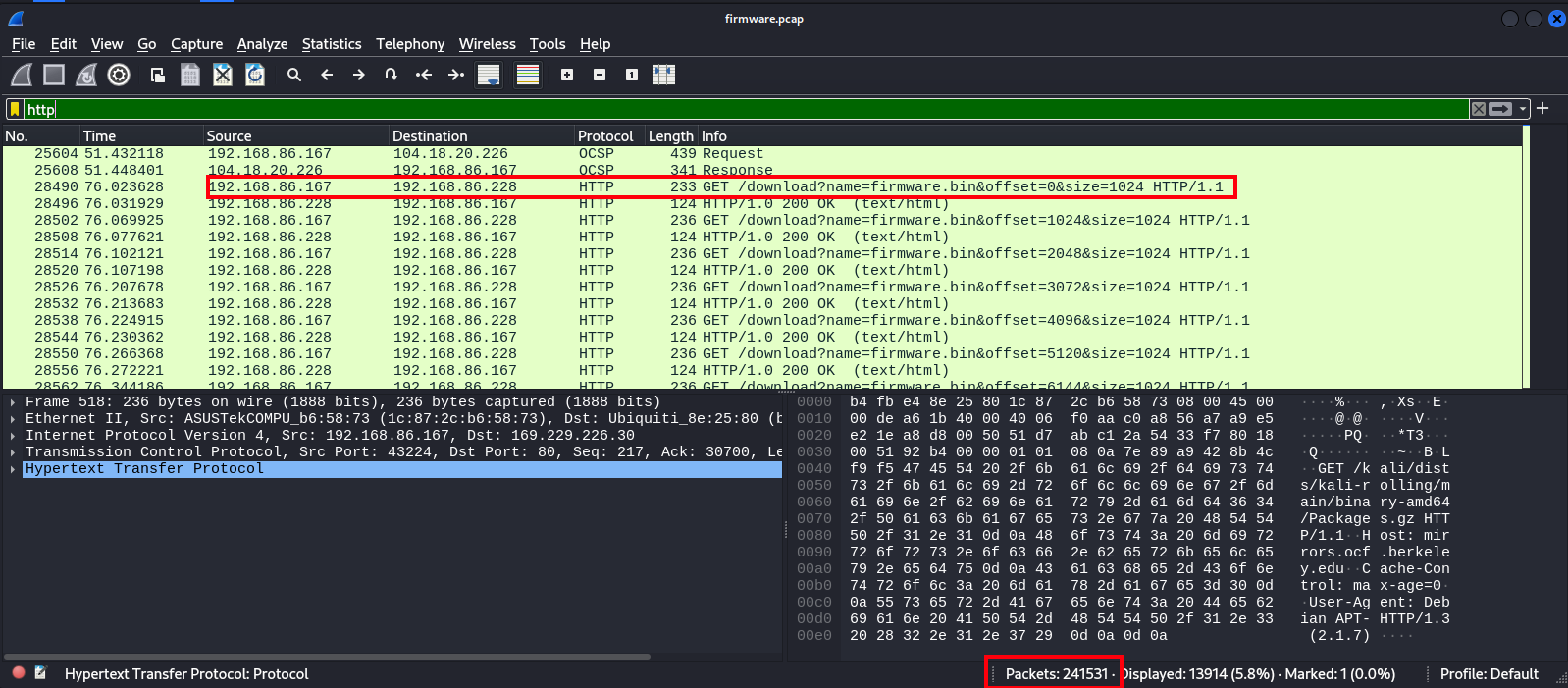
Knowing we are ultimetly looking to re-construct a firmware download, we can discern some important info from wireshark
- There are 241,531 packets in this capture, but only some are the traffic directly related to this download
- Client of the download is 192.168.86.167 and server origin is 192.168.86.228:5000
- The download is split over multiple HTTP requests by the shown convention, which themselves are split over multiple TCP requests
A starting point of a BPF might look like tcp and src host 192.168.86.228 and src port 5000 and dst host 192.168.86.167
As a wireshark filter, this would be tcp && ip.src == 192.168.86.228 && tcp.srcport == 5000 && ip.dst == 192.168.86.167
Scapy
I wrote a python scapy script will help us work with this capture file to assemble the .bin from the raw response of the relevant TCP packets. This script is shown in ./app.py. Our script will confirm the extracted binary matches the following checksums
MD5: 7aa6a7ebcbd98ce19539b668ff790655
SHA256: 2a7719719aa4f869586a7043f532e01ed4985e5c25b9a54979ac7d50c67820ec61c2805d6169b9c95a98104b8fb1d4f9ec698d23881360e99f5232a4f3cf12d4
Questions
- What architecture is the firmware intended to run on?
- What OS is the firmware running?
- What users are present on the system?